Why Cybersecurity Matters to the EV Ecosystem
Raghav Bharadwaj
Chief Executive Officer
Published on:
18 Sep, 2023
Updated on:
24 Nov, 2025

EVs have emerged as a promising solution to address climate issues, create new job opportunities, and act as an engine for economic growth. However, the increasing connectivity of EVs creates new cybersecurity risks. The recent combination of cutting-edge technologies and mobility in EVs brings new cybersecurity vulnerabilities to ensure safety, reliability, and trustworthiness.
This article talks about EV cybersecurity in India, and examines possible next steps. Specifically, it answers:
- What major cybersecurity risks do EV ecosystems face?
- Why is it important to address cybersecurity in the EV ecosystem, and how does it impact stakeholders, including EV manufacturers, charging infrastructure providers, and policymakers?
- How can stakeholders mitigate these cybersecurity risks and enhance the resilience of the EV ecosystem?
Assessing Current Cybersecurity Processes
In EVs, each individual component is connected to a central operating system. This operating system ensures smooth communication between all of the components, as well as monitoring their individual health and performance. Although this model is efficient, it also means that hackers can use the operating system as a single point of attack to bring down the entire EV. To highlight this vulnerability, a research student hacked into 25 Tesla EV cars using a third-party tool called Teslamate.
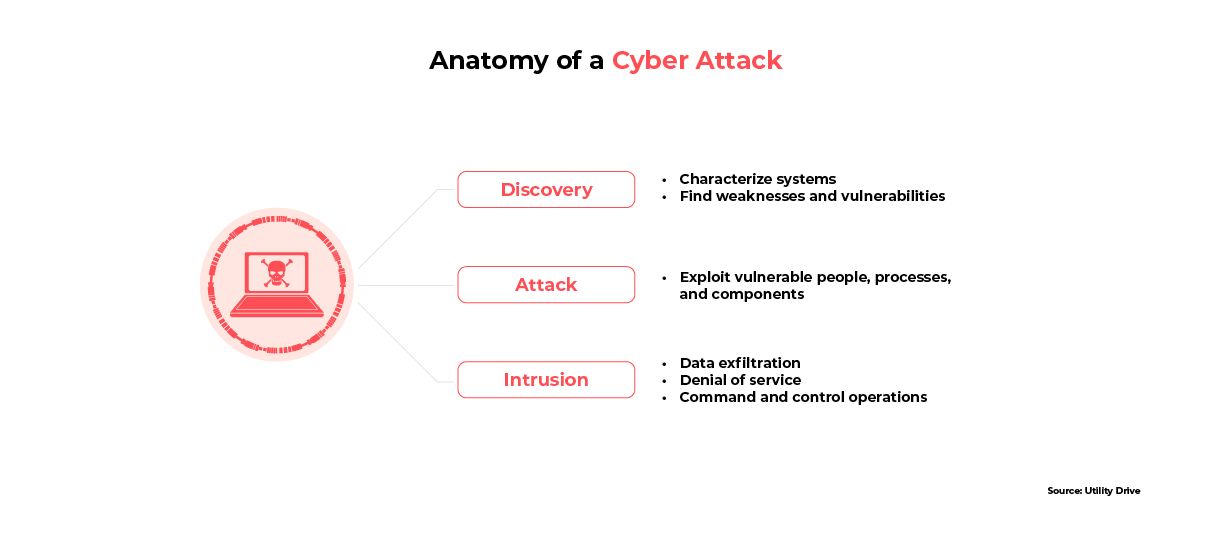
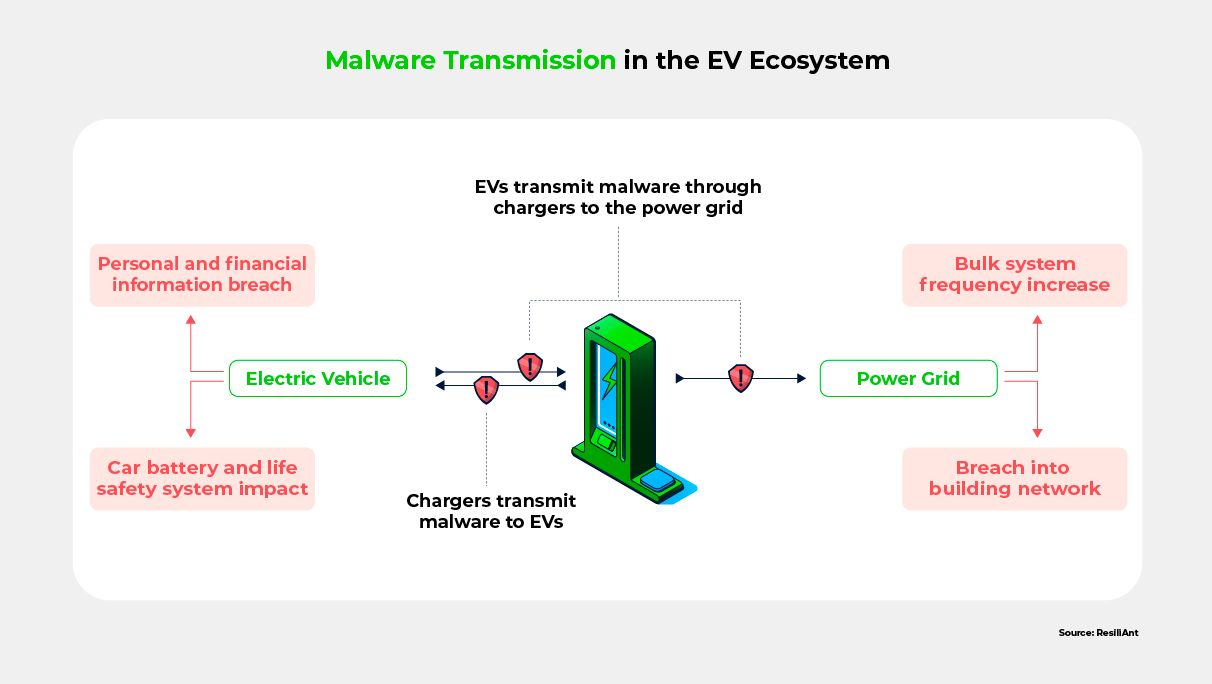
Charging infrastructure introduces additional risks. By connecting to a charger, which is necessary for monitoring charge levels and avoiding voltage fluctuations, EV operating systems become vulnerable to malware and ransomware that can be transmitted through the charger. Malware can also be transmitted in the other direction: from the infected EV to the charger, and then from the charger to the power grid. Ransomware, on the other hand, is more dangerous because cybercriminals lock the EV users’ personal data using encryption techniques and demand a high payment as ransom to provide the decryption key. Such attacks have the potential to cause large-scale power outages, similar to the Colonial Pipeline ransomware attack that inflicted fuel shortages on the United States’ east coast in 2021.
EVs are also susceptible to social engineering attacks such as phishing. One investigation discovered that scammers in India had defrauded would-be EV customers of approximately $1,000,000, by using Google Ads to misdirect them to phishing sites and charging them for down payments or booking fees for nonexistent EVs.
Although these incidents are relatively rare so far, growing EV adoption of EVs opens the door to more frequent and serious security breaches with widespread ramifications.
The Value Chain of the Indian EV Ecosystem
Cybersecurity risks can potentially discourage EV adoption, and reverse the environmental and economic gains that EVs have achieved so far. To counteract this, EV manufacturers, charging station operators, and service providers must work to earn consumers’ trust. Otherwise, they may incur reputational damage, massive financial losses, and even legal liabilities. Stakeholders who are not directly connected to EVs must also step in; cyberattacks on EVs could lead to public safety hazards such as grid blackouts, disabled EV charging infrastructure, mass malware, stolen personal information, and more.
To mitigate these risks, protect individuals and companies in the EV ecosystem, and safeguard national resources including power grids, cybersecurity for EVs is a top priority today. The first step to building a comprehensive cybersecurity solution is to understand the most likely threats to both charging networks and EVs themselves.
Major Cybersecurity Risks in EVs
EVs’ inherent architecture and design make them vulnerable to unique cybersecurity threats such as the unauthorized takeover of vehicles. Furthermore, EVs’ reliance on software puts them at risk of malware attacks and data breaches.
Hacking and Unauthorized Access to Vehicles
Most EVs unlock via either apps or RFID chips. Unfortunately, car manufacturers’ apps are demonstrably vulnerable to hacking, and RFID chips are easy to clone. This gives hackers two different mechanisms for easily gaining unauthorized access to an EV’s systems. In addition to physically unlocking the EV, they could remotely manipulate braking, acceleration, or steering functionality, potentially leading to life-threatening accidents.
Data Breaches and Privacy Concerns
EVs and their associated charging infrastructure collect and store a wealth of data, including user profiles, location data, and payment details. Cybercriminals can exploit this valuable information through wireless technology and malicious software for financial gain. This risk can hinder EV adoption by exacerbating existing public concerns about data safety, usage, and sharing.
Malware and Software Vulnerabilities
Malware can infect EVs, compromising their functionality, safety features, and data integrity. Potential consequences of these attacks range from inconvenience and financial losses to threats to public safety. Since EV components are so closely connected to other systems, hackers can inflict virtually unlimited damage.
Besides EVs, the charging networks can also be impacted by cyberattacks.
Major Cybersecurity Risks in the EV Charging Networks
The Electric Vehicle Supply Equipment (EVSE) industry is experiencing explosive growth due to the increasing demand for EV charging points. Unfortunately, due to their unique position at the intersection of the energy and transportation sectors, EVSEs are highly susceptible to cyberattacks. From cyberattackers’ perspective, EVSEs provide a perfect opportunity to cause widespread damage.
Below are some potential ways for hackers to attack EV charging networks.
Disrupting Electrical Grids
Since chargers connect to national resources like power grids, cyberattackers have the opportunity to cause major disruptions. Electrical grids are an unusually easy and attractive target for cybercriminals, since attacking them can inflict extensive damage with little effort.
Disabling EV Charging Infrastructure
Hackers can disable EV charging stations, thereby stranding drivers. The magnitude of the threat increases with every new charging station. For example, the United States’ current governmental plan to fund EV charging stations across 53,000 miles of highways will give hackers myriad opportunities to disrupt operations.
Accessing Interconnected Systems
The EVSE architecture encompasses a variety of components and architecture types. For example, some EVSE equipment may use renewable energy resources, or may be connected to building management systems. This interconnected architecture means that, by gaining access to a single charger, hackers can attack an entire system.
All of these threats require comprehensive solutions, both to protect public safety, and to build confidence and trust among potential EV owners.
Addressing Key Cybersecurity Challenges in the EV Ecosystem
Overcoming the above cybersecurity challenges requires a proactive and multifaceted approach from all stakeholders. Given the dynamic nature of cyber threats, the complexities in implementing solutions, and the lack of awareness about the underlying problem, collaboration is crucial now.
Dynamic Nature of Cyber Threats
The growing sophistication of EV components and technologies continually opens new attack vectors for cybercriminals. To effectively combat these ever-evolving threats, continuous monitoring, threat intelligence, and adaptive security measures are essential. Continuous monitoring of communication channels allows for real-time detection and response to potential attacks, while threat intelligence provides insights into new risks and trends. Cybersecurity teams are taking a proactive approach by alerting drivers of potential breaches and using SAE automation levels 1-3 to mitigate them automatically.
Implementing adaptive security measures ensures the ability to effectively address cyber threats as they emerge. Due to the rapid pace of technological advancements, however, staying abreast of the latest cybersecurity best practices and industry standards poses its own challenges. As a result, collaboration between stakeholders, including manufacturers, cybersecurity experts, and regulatory bodies, is essential to disseminate and implement up-to-date guidelines and standards that protect the privacy of users.
Complexities in Securing the EV Ecosystem
Securing the EV ecosystem is complex because of the diverse components and systems involved. It is crucial to implement measures and checks not only within every individual system, but also at the endpoints where systems integrate with each other. In particular, the communication networks that connect systems are highly vulnerable and impactful targets, and therefore require secure protocols and encryption to prevent interception or tampering.
Furthermore, backend systems managing EV data and infrastructure operations need robust protection like secure tools, VPNs, and role-based access to ensure data integrity and availability. Overall, a holistic security approach that takes into consideration the interdependency between components is necessary for the integrity and resilience of the entire EV ecosystem.
Lack of Awareness
Most stakeholders today are not aware of the cybersecurity risks associated with the EV ecosystem. Accordingly, a vital first step is to raise awareness about EV cybersecurity, so that stakeholders can make informed decisions and take necessary precautions. Educating EV manufacturers and charging infrastructure providers about cybersecurity best practices can facilitate the implementation of robust security measures at the design and operational levels.
Policymakers need to be aware of these risks, so that they can develop regulations and standards that prioritize cybersecurity in the EV ecosystem. Furthermore, consumers must be informed about the importance of adopting secure practices and encouraging them to adopt them Some ways for users to protect their data are:
- Regularly update software, as they become available
- Use strong passwords
- Know how to identify compromised chargers and be on the lookout for these signs
- Beware of phishing emails and messages
Comprehensive awareness campaigns, training programs, and information-sharing platforms can also boost awareness among all of these stakeholders.
As part of the cybersecurity process, automakers, charging point manufacturers, and OEMs must be encouraged to implement cybersecurity measures at every stage of their operations.
Implementing Effective Cybersecurity Measures
Cybersecurity principles must be an integral part of every software development and manufacturing activity. Secure design principles can lay the roadmap for development while the use of encryption and authentication can reduce the attack surface. All these measures must be tied in with awareness and education, so that end users can avoid risky behavior.
Secure Design Principles for EVs
“Secure by design” is a set of principles that ensure safety and reliability right from the design phase. These principles ensure that safety is not compromised for fast development.
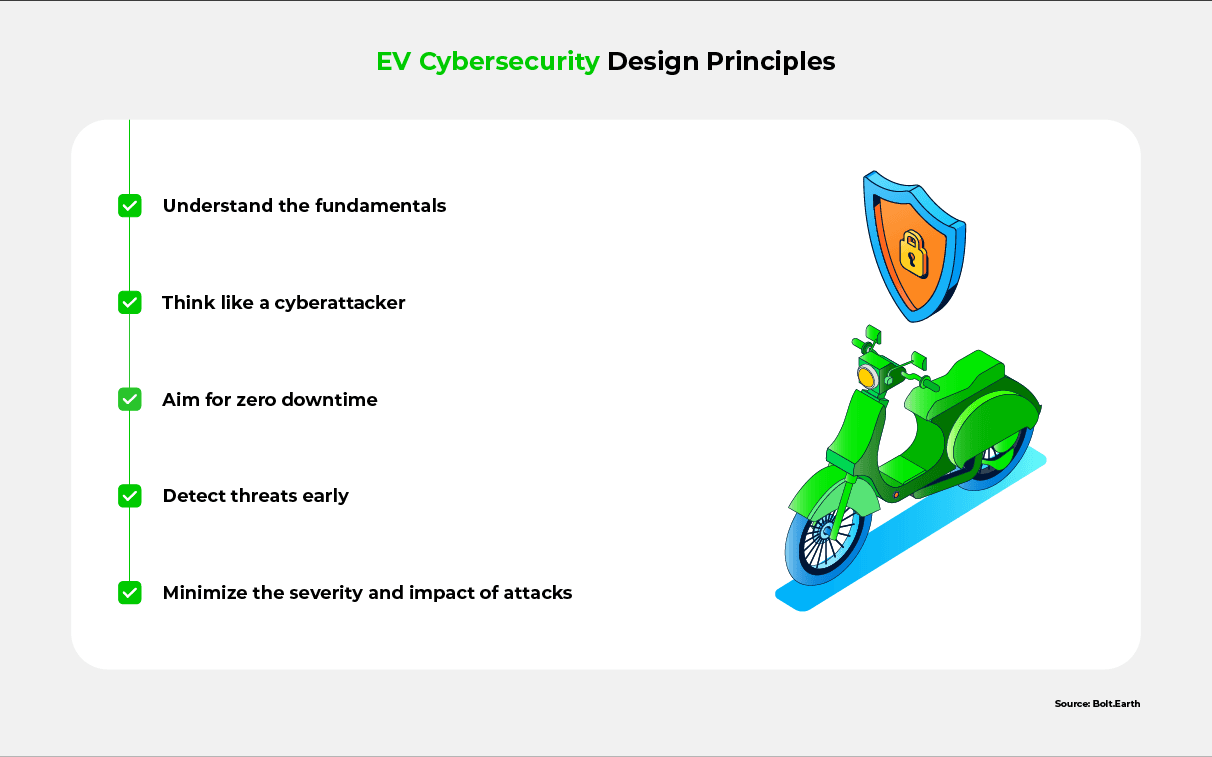
Key principles of secure design include:
- Understand the fundamentals and address any shortcomings
- Design for security by thinking like a cyberattacker
- Aim for zero downtime by ensuring that the technology cannot easily be disrupted
- Make provisions for continuous monitoring and early threat detection
- Aim to minimize the severity and impact of attacks
Encryption Technologies for Data Protection
The unique zonal and interconnected system architecture of EVs requires out-of-the-box solutions for data protection. Relevant security techniques include:
- A zero-trust approach, where every user or device must establish its identity to access a resource
- Advanced privacy-preserving frameworks like L-EncDB
- Blockchain-based systems for greater visibility into data access and modification
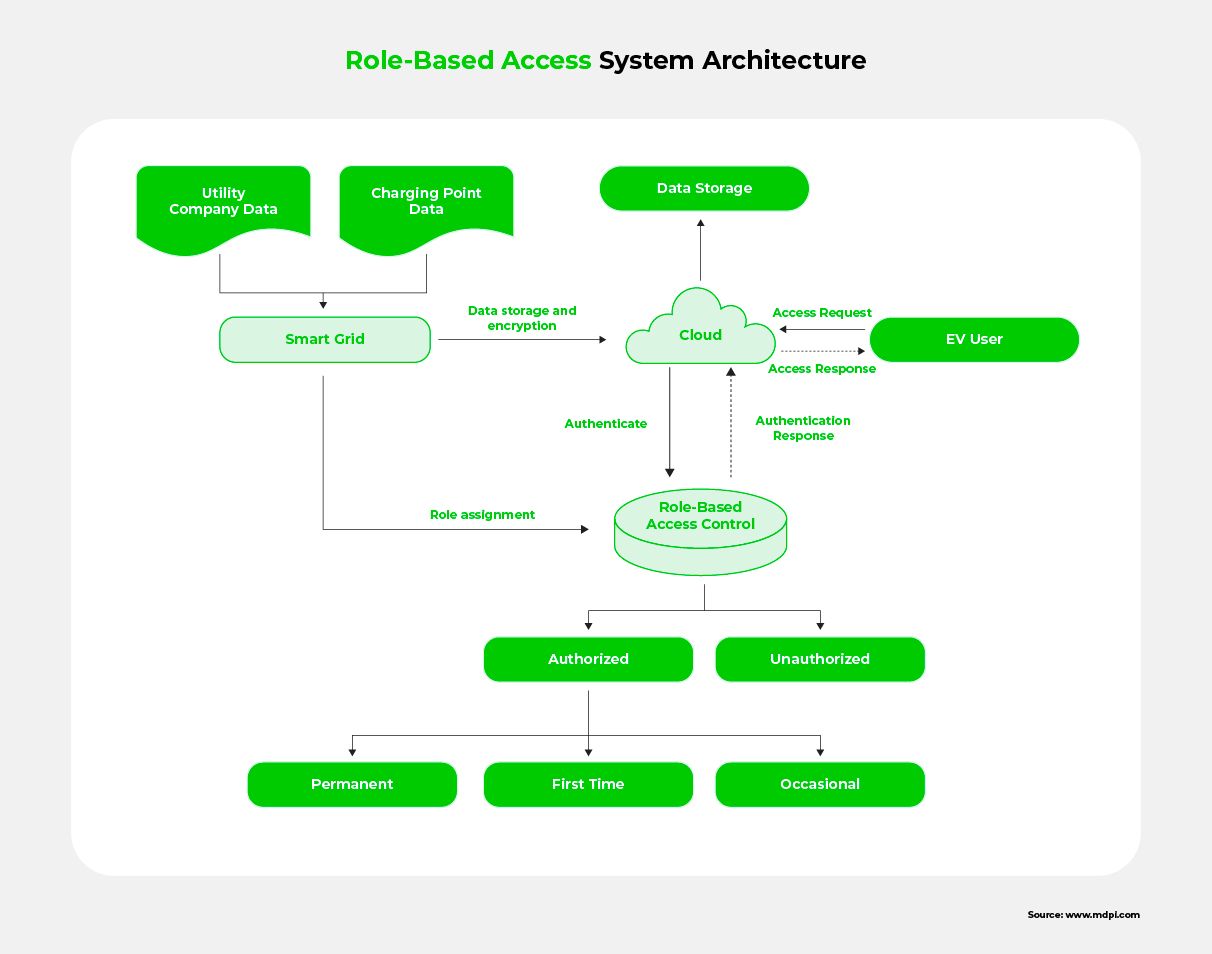
- A smart role-based access system that combines authentication and authorization strategies to prevent illegal access to data
- Advanced encryption mechanisms
Regular Software Updates and Patches
Given that EVs rely greatly on software for their smooth running, automakers and software developers can enhance security and add new features through regular software updates. Participants in this process should:
- Stay on top of imminent attacks and vulnerabilities, and build updates to address them
- While designing software, ensure compatibility across different EV models
- Consider using a technology-agnostic open-source OS
- Integrate intelligent chips into EVs to make them capable of receiving both software and firmware OTA updates
- Work with EV manufacturers, charging infrastructure providers, and software developers to seamlessly deliver timely updates and patches
Implementing the above security measures can go a long way in improving the safety and resilience of EVs, that in turn, can promote their growth and adoption.
Promoting Resilience and Growth in the EV Ecosystem through Cybersecurity
As the world anticipates the EV ecosystem’s environmental and economic benefits, cybersecurity emerges as a crucial component in promoting resilience, growth, and sustainability in EVs. The potential economic growth associated with a secure and resilient EV ecosystem is immense, attracting investments and fostering innovation that will drive job creation and economic development.
Simultaneously, increased EV adoption and reduced reliance on fossil fuels will have a substantial positive impact on the environment. None of these benefits, however, are attainable in the absence of a robust cybersecurity foundation. In this sense, cybersecurity serves as the bedrock for fostering trust among consumers, encouraging widespread EV adoption, and ensuring a sustainable transportation future.
All EV stakeholders must prioritize cybersecurity measures to build a resilient EV ecosystem that inspires confidence, drives economic prosperity, and paves the way for a cleaner, greener, and more sustainable world. The moment has come to embrace cybersecurity as a catalyst for transforming the EV landscape and shaping a brighter future for transportation.
To learn more about cybersecurity for EVs, see the FAQs and Resources below!
FAQ
What are the cybersecurity risks to the EV ecosystem?
EV cybersecurity risks include unauthorized vehicle takeover through keyless access mechanisms, compromised vehicle controls, and theft of personal data. EV charging system cybersecurity risks include power grid disruptions, data breaches, access to interconnected systems like renewable energy sources and building management systems, and malware and ransomware attacks.
How can EVs and charging infrastructure be protected from cyber threats?
Some measures to protect EVs and charging infrastructure from cyber threats include implementing secure communication protocols, using tamper-resistant hardware, conducting regular software updates, and employing encryption technologies. Authentication mechanisms and access control systems can also prevent unauthorized access. Most importantly all stakeholders must come together to implement cybersecurity principles and techniques at each stage.
Why is cybersecurity crucial to the development of a resilient EV ecosystem?
Cybersecurity is crucial to the development of a resilient EV ecosystem because it protects against cyber threats, ensures the safety of personal data, protects national resources like the power grid, and fosters consumer trust. A resilient EV ecosystem can, in turn, enhance EV adoption, improve economic development, and create sustainable transportation for the future.
What are the potential consequences of neglecting cybersecurity in the EV ecosystem?
Neglecting cybersecurity in the EV ecosystem can have far-reaching consequences not only for individual EV owners, but also for public safety, and for the transportation and energy sectors as a whole. A lack of resilience to cyberattacks can lead prospective EV owners to worry about the safety of their data, and can therefore discourage them from EV adoption. Consequently, neglecting cybersecurity will lead to huge financial losses for automakers, OEMs, charging point operators, and others, as well as reversing the environmental gains that EVs have already made.
Are there any existing regulations or standards regarding EV cybersecurity?
Yes, there are existing regulations and standards regarding EV cybersecurity. One prominent example is the UNECE WP.29 regulation on Cybersecurity and Software Updates for Automotive Systems, which includes provisions specific to EVs. Additionally, organizations such as ISO, SAE, and NIST have developed standards and guidelines addressing cybersecurity in connected vehicles, including EVs.
How can stakeholders collaborate to build a secure and resilient EV ecosystem?
Stakeholders can collaborate to build a secure and resilient EV ecosystem by sharing information, coordinating efforts, and establishing industry-wide standards. Collaboration between EV manufacturers, charging infrastructure providers, policymakers, cybersecurity experts, and researchers is essential to build a secure EV ecosystem for the future.
Resources
Telematics Wire: Cybersecurity Assessment for EV Ecosystem – End-to-End Approach
Find an in-depth examination of EV cybersecurity.
Corporate Compliance Insights: Electric Vehicle Charging Stations: Unexpected Target for Cyber Attacks?
Read about potential cybersecurity attacks on EV charging stations.
arXiv: An Overview of Cyber Security and Privacy on the Electric Vehicle Charging Infrastructure
Learn more about the EV ecosystem’s need for cybersecurity.
ElaadNL: Knowledge and Innovation Center for Cybersecurity in Connected Vehicles
Understand how ElaadNL is empowering stakeholders to tackle cybersecurity challenges.
OSTI: Cybersecurity for EV Charging Infrastructure
Discover recommendations for boosting the cybersecurity of EV charging infrastructure.





