EV Charging Cybersecurity in India: Threats, Risks, and Policy Landscape
Raghav Bharadwaj
Chief Executive Officer
Published on:
13 Nov, 2025
Updated on:
10 Feb, 2026

India’s electric mobility network is growing at lightning speed, with thousands of public chargers powering millions of EVs daily. As chargers become smarter and more connected, they also become prime targets for cyber threats. From data breaches to remote tampering, a single compromised station can disrupt networks or expose sensitive information. Securing India’s charging ecosystem is now as essential as maintaining grid stability or fire safety.
In this blog, we explore:
- Why cybersecurity matters for EV charging in India, and how attacks on connected chargers could compromise charging networks and infrastructure.
- India’s evolving policy and standards landscape and secure communication protocols.
Why Cybersecurity Matters for EV Charging in India
India’s EV ecosystem is growing fast, with nearly 2 million EVs sold in FY2024-25 and over 29,000 public charging stations operational by late 2025. The government’s PM E-Drive program aims to install 72,000+ public chargers by 2026.
Each charging point is an IoT-enabled device that connects with vehicles, payment systems, and the power grid. This connectivity brings convenience but also makes chargers enticing targets for cybercriminals. A single compromised charger could lead to stolen user data, disrupted charging services, or even grid instability. In short, cybersecurity has become as important as electrical safety in the EV charging domain.
Government and industry stakeholders recognize the stakes. In 2023, Transport Minister Nitin Gadkari cautioned Parliament that EV charging stations are “susceptible to cyberattacks and security incidents, just like any other technological application.” He noted that India’s Computer Emergency Response Team (CERT-In) has already observed vulnerabilities in charging station software/hardware and issued multiple security alerts with countermeasures. Reporting cyber incidents is now mandatory, and the government is “actively taking steps to combat the issue of hacking”, emphasizing that securing EV infrastructure is a national priority.
Major Cyber Risks Facing EV Charging Networks
What kind of cyber threats do EV charging networks face? Broadly, the risks mirror those in other IoT and critical infrastructure systems. Key threat vectors include:
1. Denial-of-Service (DoS) Attacks
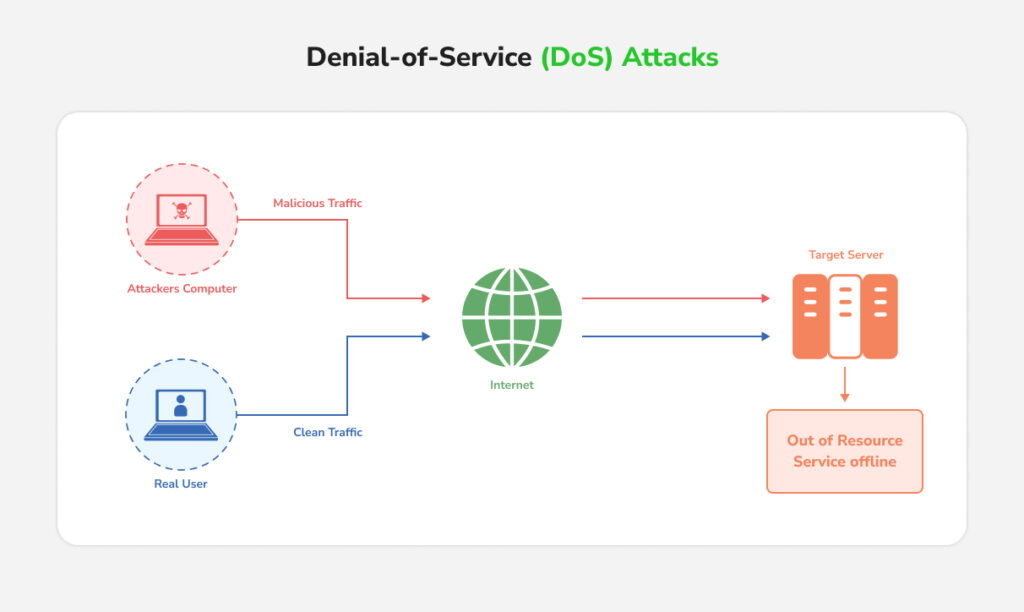
Overloading servers or communication channels to knock chargers offline. For instance, in a 2023 incident, ransomware attackers temporarily shut down a major charging network across the US and Europe. In a coordinated attack, widespread charger outages could even strain the grid by suddenly dropping or spiking demand.
2. Man-in-the-Middle (MitM) Attacks
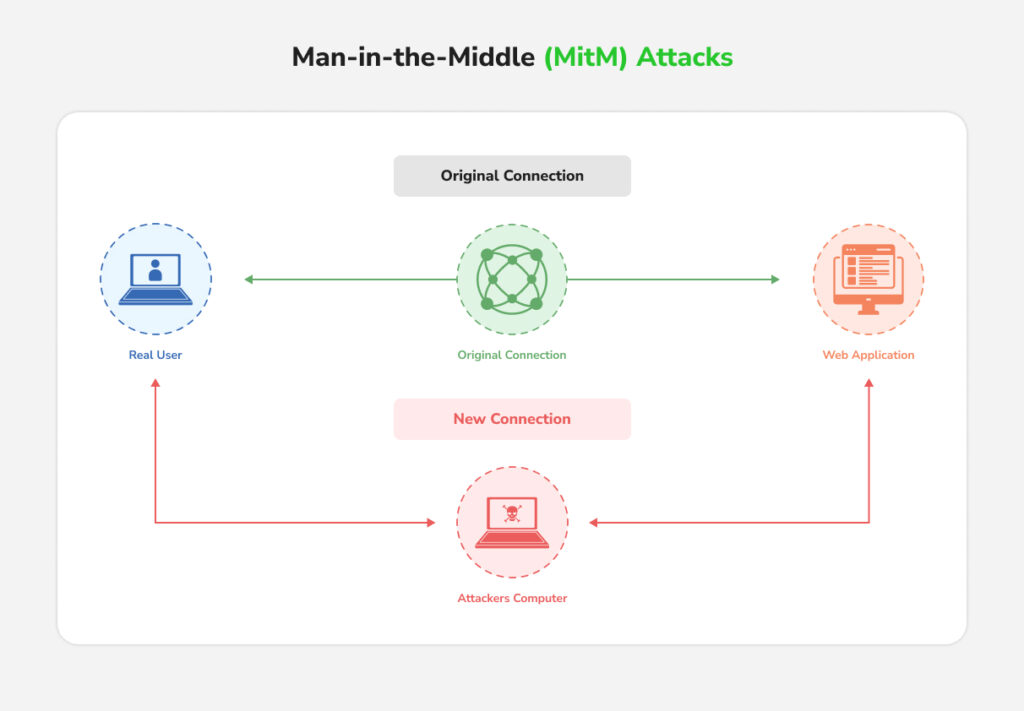
Hackers intercept communication between EV chargers and backend systems to steal sensitive data (like payment information or user credentials) or send fraudulent commands. For instance, an attacker relaying or altering messages could manipulate charging session data, leading to incorrect billing or unauthorized free charging.
3. Malware and Ransomware
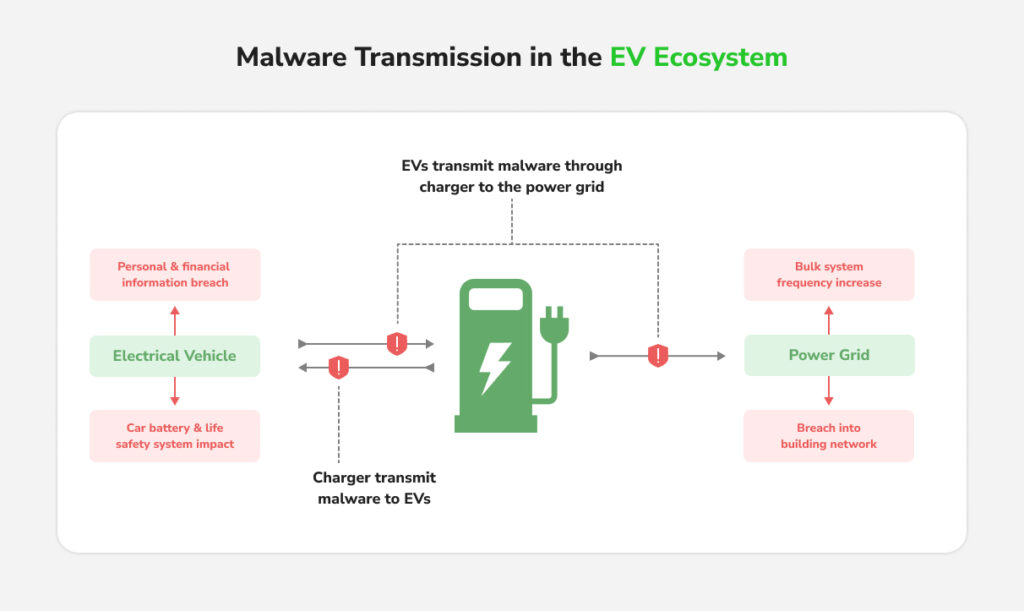
Chargers run software that can be infected just like any computer. Ransomware can lock down operations until a ransom is paid. A notable real-world example occurred in 2023 when a charging network provider was hit with ransomware that turned off chargers across multiple countries and demanded cryptocurrency to restore service. The company recovered without paying, but the incident was a wake-up call.
4. Data Breaches
Public chargers often handle user identities, credit card payments, and vehicle data. Poorly secured systems can expose user identities, payment details, or charging patterns. In one case, Shell’s charging network had a vulnerability that could have exposed millions of charging session logs, including potentially sensitive driver data, before it was patched.
5. Unauthorized Remote Control
If attackers exploit software vulnerabilities in a charger or the connected vehicle, they might gain remote control of charging equipment or even the vehicle. This scenario is more complex but was demonstrated when researchers at a 2025 cybersecurity contest compromised Tesla home chargers, highlighting that even widely used EVSE systems had exploitable flaws. In extreme cases, such exploits could be used to manipulate the charging rate or harm vehicle batteries (like overcharging) or as a bridge to infiltrate the car’s internal network.
6. Supply Chain Backdoors
Another risk specific to India’s context is the heavy reliance on imported charger components. About 80–85% of EV charger parts in India are sourced from abroad (mainly China), raising concerns about hidden malware or backdoors. Industry experts warn that malicious code implanted in a charger’s components could be activated later to compromise the charger or any network it connects to.
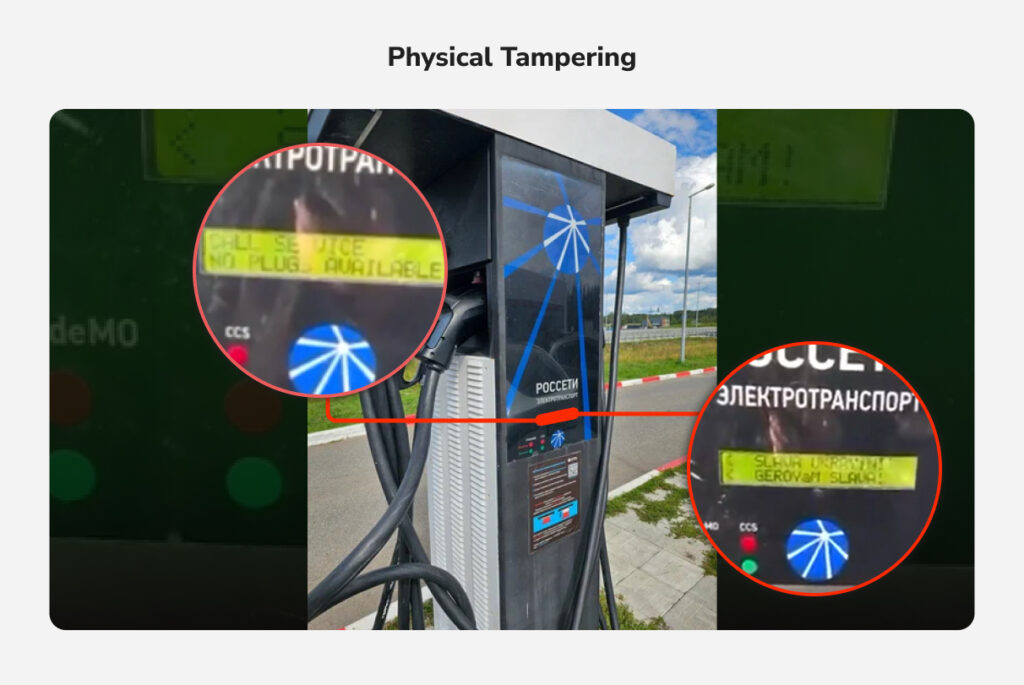
7. Physical Tampering
Not all attacks are purely digital; exposed chargers can be physically tampered with. For example, installing skimmers (to steal card data) or malware devices. Proper locks, tamper alarms, and surveillance can mitigate these risks, but they remain a consideration, especially for private chargers in unguarded locations.
Real-world incidents highlight these threats. In 2022, EV chargers in Russia and the UK were hacked to display rogue political messages. While these were pranks, the attackers essentially took control of the stations’ interfaces remotely, a capability that could be misused for more damaging ends.
More recently, Electrify America (a major US charging network) faced shutdowns due to operating system weaknesses, and in 2025, researchers at Pwn2Own (Tokyo) successfully breached Tesla’s Wall Connector chargers twice. Although India has not yet seen large-scale charger hacks, these examples highlight the urgent need for robust cyber protections.

India’s Policy and Standards Landscape for EV Charging Security
Ensuring cybersecurity in EV infrastructure is a shared responsibility, and the Indian government has laid groundwork through policies and standards:
Ministry of Power (MoP) Guidelines
Issued in 2018 and revised in 2022 and 2024, these guidelines standardize charger deployment across India. While the MoP guidelines do not explicitly focus on cybersecurity, they enforce quality and uniformity, creating a reliable foundation on which software security can be built. Notably, under these guidelines no license is required to operate public chargers, making it even more important that operators voluntarily adhere to best practices.
Bureau of Indian Standards (BIS) Certifications
The BIS has developed an entire set of standards (IS 17017 series, mirroring IEC 61851 and others) that cover performance, safety, and connector requirements for EV chargers. Adherence to these standards is now mandatory for manufacturers. Although these are largely electrical and mechanical standards, compliance ensures that chargers have proper protections against electrical surges, faults, and basic tampering. Robust hardware reduces risks of unsafe behavior during cyberattacks. BIS is also exploring standards for communication protocols and data security in automotive electronics.
CERT-In Directives and Cyber Guidelines
India’s CERT-In (Computer Emergency Response Team) under the IT Ministry plays a key role in cybersecurity policy, including for EV infrastructure. CERT-In continuously issues alerts and advisories about the latest cyber threats to EV charging systems and recommended countermeasures. Importantly, in 2022 the government empowered CERT-In to mandate that all cybersecurity incidents must be reported within hours and to prescribe emergency measures.
Gadkari highlighted that CERT-In has “formulated a Cyber Crisis Management Plan” for critical sectors and empaneled 150 security auditors to help organizations tighten their defenses. For charging network operators, this means any breach or malware outbreak in their network must be disclosed to CERT-In, and they should follow CERT-In’s best practice guidelines. In 2024, the Ministry of Road Transport and Highways (MoRTH) explicitly acknowledged the cyber threat to EV chargers and stated that charging networks are expected to comply with CERT-In’s advisories, such as implementing encrypted communication, strong authentication, and regular security patches. While there isn’t a dedicated “EV charging cybersecurity law” yet, these directives effectively compel CPOs to adopt standard cyber hygiene or risk regulatory action.
Emerging EV Communication Standards
India is encouraging the adoption of secure communication standards like OCPP and ISO 15118 in its EV ecosystem. Open Charge Point Protocol (OCPP) is the common language between chargers and their central management system. The latest version, OCPP 2.0.1/2.1 (released in 2025), adds substantial security features. It supports secure boot, encrypted messaging (TLS), digital certificates for charger authentication, and even secure firmware update mechanisms.
Many Indian networks today still use OCPP 1.6, but new installations are increasingly expected to use OCPP with security profiles enabled. Likewise, ISO 15118, the global standard for vehicle-to-charger communication, uses a robust PKI-based encryption and authentication system for EVs and charging points. The Bureau of Energy Efficiency (BEE) and other bodies have run pilots on ISO 15118 features in India, given its potential to make public charging both seamless and secure. Though ISO 15118 is not yet universally deployed, its secure handshake and cryptographic authentication offer a blueprint for the future of EV charging in India. We can expect upcoming guidelines to formally recommend these protocols for any smart public charging infrastructure.
No Dedicated EV Charger Cyber Law – Yet
It’s worth noting that as of late 2025, there is no separate cybersecurity certification or regulation specifically for EV chargers. General IT security rules apply, and power sector regulations cover grid-safety aspects. Industry executives have pointed out this gap, suggesting that specific guidelines could emerge as the network expands. In the meantime, much of the responsibility lies with charger manufacturers and operators to proactively secure their infrastructure.
Final Thoughts
The cyber risks are real and evolving, from ransomware attacks and data breaches to potential grid disruptions. But so are the solutions. With proactive implementation of secure communication standards like OCPP 2.0.1 and ISO 15118, adherence to CERT-In directives, and consistent alignment with BIS and MoP frameworks, India has the tools to stay ahead of emerging threats.
Ultimately, cybersecurity in EV charging is not a one-time compliance exercise; it’s a continuous process of vigilance, collaboration, and innovation. As stakeholders across government, utilities, OEMs, and CPOs work together, India can build a charging network that’s not just widespread and reliable but also cyber-resilient. Protecting this digital backbone today will ensure that tomorrow’s electric highways remain open, safe, and secure for all.

Frequently Asked Questions
Why can’t imported components just be “checked” for malware before use?
Because backdoors are often embedded deep in firmware or chipsets —invisible without advanced testing. India is working toward local manufacturing and stronger supply chain audits to close this gap.
If India doesn’t have a dedicated EV cybersecurity law yet, who enforces compliance right now?
Currently, CERT-In acts as the de facto authority. It mandates that all cyber incidents must be reported and issues security advisories that operators are expected to follow. Enforcement is indirect, through policy pressure, public procurement standards, and utility-level compliance.
What happens if a public charger is hacked? Who’s liable?
Right now, liability is murky. Without a dedicated law, responsibility could fall on the CPO (Charge Point Operator) or hardware vendor, depending on the cause, whether it’s poor software maintenance or a faulty device. Future EV-specific regulation is expected to clarify this.

Feb 19, 2026 • EV Charging Infrastructure
EV Charging for Quick Commerce Fleets in India: Scaling Sustainable Delivery
Read More
Feb 17, 2026 • EV Charging Infrastructure
The Psychology of EV Charging: What EV Drivers Want at a Charging Station
Read More
Feb 12, 2026 • EV Charging Infrastructure
What Is the Real Bottleneck in Scaling India’s EV Charging Network?
Read More

