9 Best Practices to Secure EV Charging Infrastructure in India
Raghav Bharadwaj
Chief Executive Officer
Published on:
14 Nov, 2025
Updated on:
10 Feb, 2026

If you’ve been following our blog series, you’ll remember our recent post, “EV Charging Cybersecurity in India: Threats, Risks, and Policy Landscape”. That piece unpacked why cybersecurity matters in EV charging, the threat landscape, vulnerabilities, and India’s evolving policy and standards.
This blog goes a step further and focuses on:
- How to protect the charging infrastructure
- Practical measures that CPOs, OEMs, and DISCOMs can implement to strengthen cybersecurity across India’s charging infrastructure.
- How networks can be designed to detect, respond to, and recover from cyber incidents.
- The roles that standards, government policy, and user awareness play in building a safe and trusted EV ecosystem.
Let’s dive in.
Stakeholder Roles in Safeguarding the Charging Infrastructure
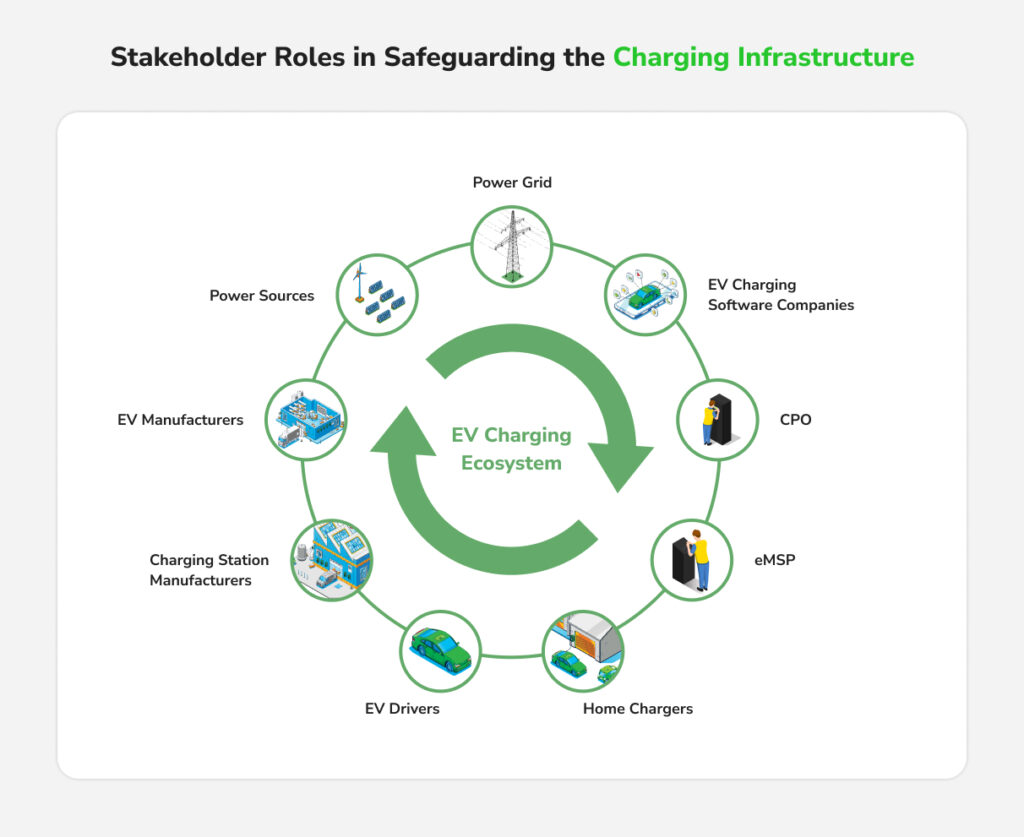
Cybersecurity for EV infrastructure is a team sport. Various stakeholders, from power utilities to device manufacturers, have distinct but complementary roles to play. The key stakeholders include:
Distribution Companies (DISCOMs)
DISCOMs (the power utilities) integrate charging stations into the electrical grid and must ensure large charging installations meet both electrical and cybersecurity standards. Communication between DISCOMs and aggregators must be encrypted and authenticated to prevent spoofing. DISCOMs can also share threat intelligence via NCIIPC or sectoral CERTs about any grid-related cyber threats that could affect charging infrastructure. As guardians of grid stability, they must treat public charging hubs as extensions of critical infrastructure, enforcing proper cybersecurity compliance as part of grid interconnection agreements.
Charge Point Operators (CPOs) and Aggregators
CPOs operate charging stations, and aggregators may manage a network of stations or provide a platform that unifies multiple CPO networks for users. They are on the frontlines of EV charging cybersecurity. CPOs should implement the best practices (discussed below) in their day-to-day operations. They must vet backend platforms for security and data protection. Follow secure coding practices and protect API keys. Coordination with DISCOMs and OEMs is essential, especially when recalls or updates affect charging security. CPOs also have a customer-facing role and should communicate their security measures clearly to build user trust.
OEMs (Equipment Manufacturers and EV Makers)
Original equipment manufacturers (OEMs), including charger hardware makers and EV automotive companies, must design chargers with strong cyber defenses and conduct thorough testing for vulnerabilities before selling units. With any Indian charger OEM relying on imported components, supply chain security is critical. India’s localization push (under schemes like PMP) is encouraging domestic production, which improves security oversight. Auto OEMs must ensure their Battery Management System (BMS) and in-car chargers reject illegitimate commands and collaborate with charger OEMs to set secure interface standards. In effect, OEMs provide the first line of defense; if they deliver secure-by-design products, the burden on operators and end-users is lesser.
Government and Regulators
Besides MoP and CERT-In, other bodies like the Ministry of Heavy Industries (MHI) and the Ministry of New & Renewable Energy (MNRE) influence cybersecurity outcomes through guidelines, incentives, and reporting mandates.
Standards organizations (BIS, Automotive Research Association of India) continue to update technical protocols. Designating major charging networks or central management systems as ‘critical infrastructure’ could bring additional safeguards. Ultimately, daily vigilance by operators and manufacturers remains critical.
9 Best Practices to Strengthen EV Charging Cybersecurity

Below are some best practices and protocols – spanning hardware, software, and operational processes – that can significantly raise the cybersecurity bar:
1. Secure Hardware and Physical Safety

Use only BIS-certified chargers with built-in safety features like voltage surge protectors, ground fault detectors, and emergency shutoffs. Ensure tamper-resistant design, locked enclosures for ports, secure boot chips that prevent unauthorized firmware from running, and intrusion sensors. Install chargers in well-lit, monitored areas, and protect the charger’s control unit from overheating or damage.
2. Encrypted Communication
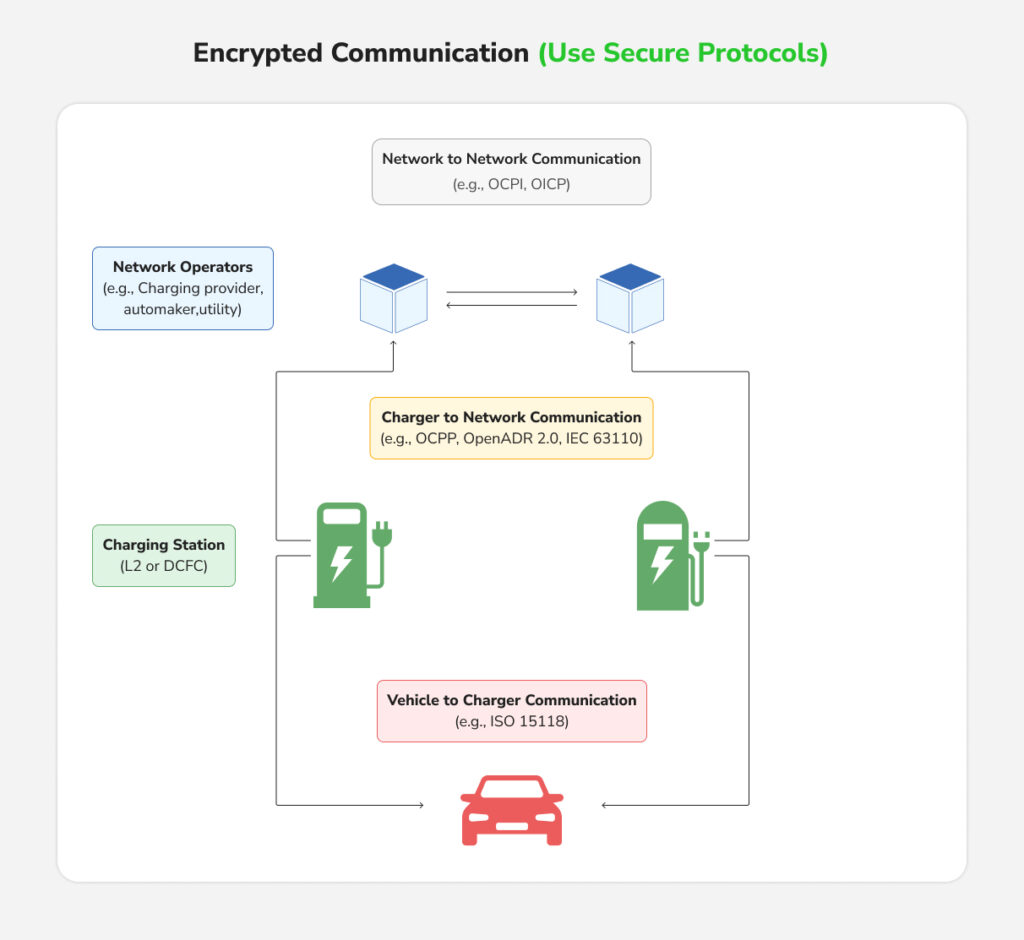
All data exchanged between the EV, the charger, and the backend server should be encrypted to prevent eavesdropping or tampering. Enable TLS encryption for all data exchanges. Use digital certificates for mutual authentication between chargers and backend systems. Segregate the charging network from the corporate IT systems and deploy a firewall to limit exposure.
3. Strong Authentication and Access Control
Charging systems should enforce multi-factor authentication for operator logins. Change default passwords, disable unused ports, and use whitelist-based communication between chargers and servers. Prevent unauthorized firmware updates or remote commands.
4. Regular Software Updates and Patching
Just like a smartphone or PC, EV chargers and their management software require regular updates to fix security bugs. CPOs should establish a policy for frequent firmware updates and prompt patching of backend systems. Use cryptographically signed OTA (over-the-air) updates to ensure authenticity. Never ignore security bulletins: for example, if a charger vendor or CERT-In announces a vulnerability in a certain model, prioritize applying the patch or mitigation provided. Maintain an inventory of all chargers, models, and firmware versions, and monitor available updates.
5. Network Monitoring and Incident Response
It’s crucial to continuously monitor charging networks for suspicious activity. Deploy intrusion detection and prevention systems (IDPS) or enable real-time logging and alerts. For example, monitor anomalies like repeated failed transactions or unusual message patterns. Train staff to recognize signs of compromise and practice incident response drills. Notify CERT-In (as required by law) and inform any affected users. Just as importantly, practice your response with drills. Quick detection and containment can mean the difference between a minor incident and a cascade of failures.
6. Secure Payment and User Data Handling
Since many public chargers handle payments (via apps, RFID cards, or credit card swipes), applying fintech-grade security is non-negotiable. Encrypt payment data in transit and at rest; use PCI-DSS compliant payment gateways and avoid storing sensitive user info on the charger’s local memory. Detect skimming devices and educate users via signage or app notifications about basic safety practices.
7. Resilience and Fail-safes
Building resilience into the charging infrastructure can reduce the impact of cyber incidents. Design backup communication channels and standby chargers for critical hubs. Implement load management algorithms to isolate chargers behaving erratically. Plan for the worst-case scenarios to ensure service continuity and grid stability.
8. “Security by Design” and Testing

Manufacturers and software developers must adopt a security-by-design approach. Implement secure coding practices and conduct threat modeling during development. Perform penetration testing before deployment. Use CERT-In empaneled security auditors for regular evaluations. Treat security as an ongoing process and not a one-time checkbox.
9. User and Staff Awareness
Even a highly secure system can be undermined by human error or ignorance. Train staff and technicians on cybersecurity basics, for example, password hygiene, update protocols, and phishing recognition. Similarly, inform fleets and users about security features and encourage the use of official apps. In a consumer-facing industry, transparency helps. Explain the signs of a tampered station and assure them that their data is protected. You can display a “security commitment” at charging stations to build trust and enlist user vigilance. By implementing these best practices, India’s EV charging providers can significantly reduce risk and build trust in the charging network. As one industry CEO put it, a charger today “is not just a power device; it is a digital interface that talks to the vehicle, the grid, and the user’s app.”
Final Thoughts
India is on the cusp of a massive EV charging expansion, and with it comes the responsibility to preempt cyber threats. The good news is that the solutions are at hand, from secure protocols and standards to proactive industry measures and policy directives. The key is execution: stakeholders must work in concert to implement these cyber safeguards at every level of the EV charging value chain. A secure charging infrastructure not only protects the grid and consumers but also fortifies confidence in India’s green mobility transition. By treating EV chargers as critical smart infrastructure and following the “Charger Protection 101” principles, India can power up with confidence, ensuring that the electric journey from Kashmir to Kanyakumari is both smooth and secure.






